Aerospike application security best practices
Discover essential Aerospike application security practices for developers in finance and healthcare, including authentication, password protection, and data encryption in transit.
Customers trust Aerospike with mission-critical and highly sensitive data in industries such as financial services and healthcare. As such, it should come as no surprise that the Aerospike Database has a full suite of enterprise-grade security features.
In this post, I’ll highlight the security best practices that you, as an application developer, need to know about when building applications with security and compliance in mind.
Use Aerospike authentication
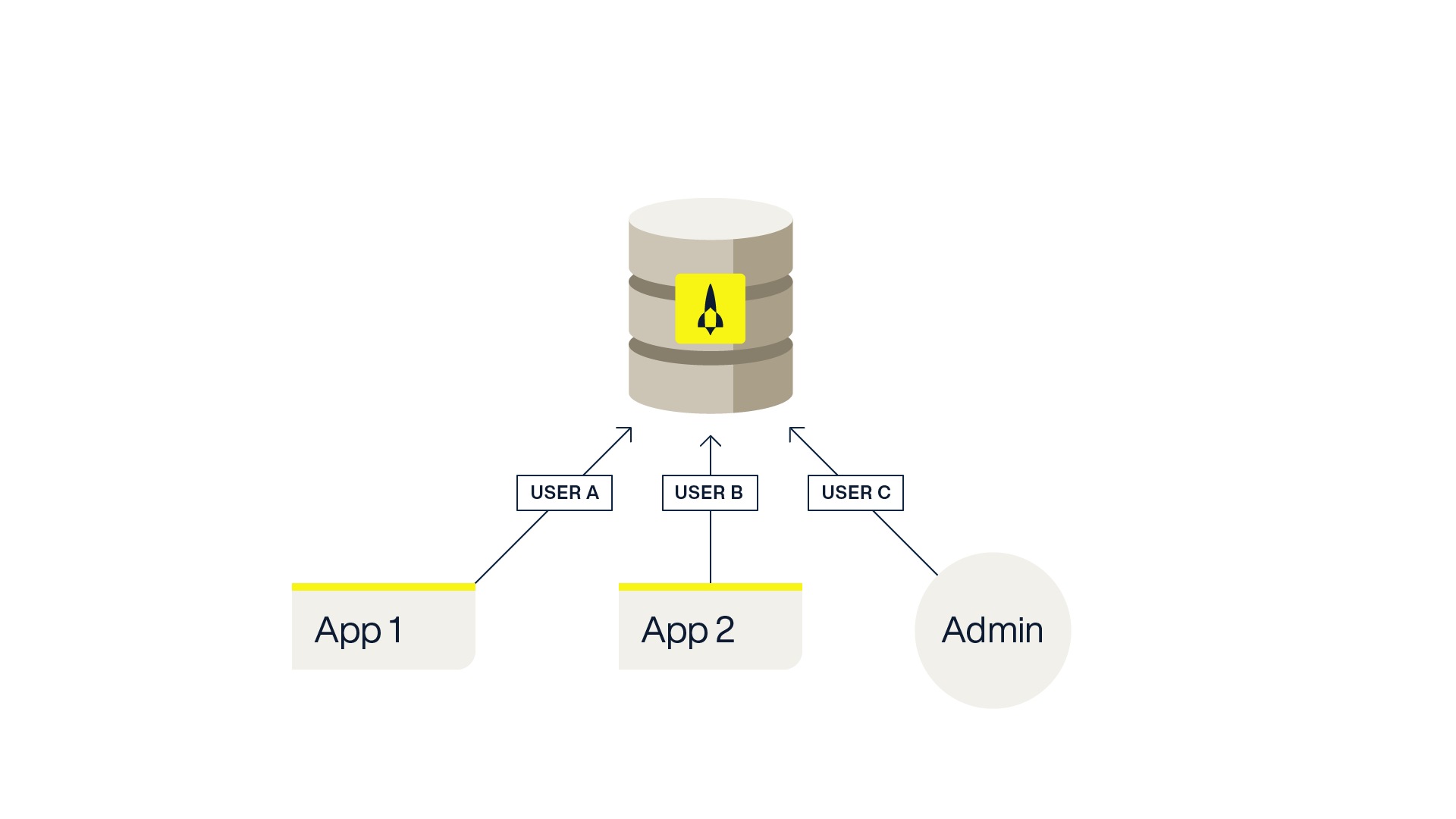
Each application and each user should use a unique Aerospike Database user. This isolates the impact of a credential leak to just the one application and allows for access controls to be applied on a per-user basis.
When using Aerospike Cloud, user authentication is always enabled, and the credentials the application uses are referred to as “API keys.”
Protect passwords
When provisioning database credentials for a user or an application, use strong passwords and protect passwords from unauthorized access. Passwords should not be hard-coded or stored on the filesystem.
Option 1: Use a secret manager
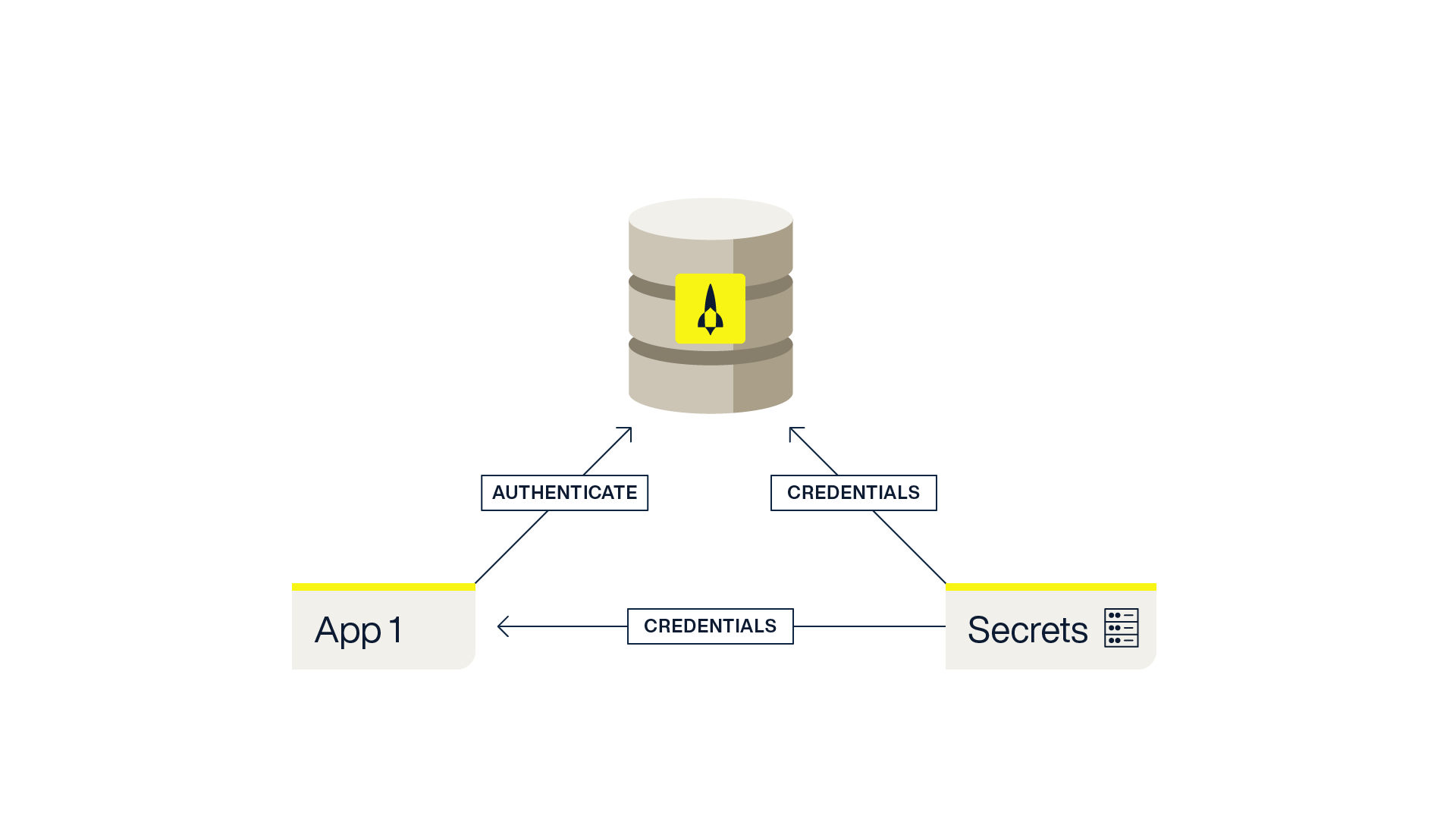
A common approach to safeguarding passwords is to integrate with the secret management solution provided by cloud providers such as AWS Secrets Manager and GCP Secret Manager.
Hashicorp Vault is often used as a multi-cloud and hybrid cloud secret management solution. In fact, Aerospike uses Hashicorp Vault in Aerospike Cloud Managed Services and Aerospike Cloud.
Regardless of which of these solutions you choose for managing the secrets used by your application, the Aerospike Database will also be able to integrate with the same solution using Aerospike Secret Agent. Secret Agent provides an abstract interface to multiple secret managers, including those mentioned above.
In addition to secret management, Hashicorp Vault also supports the concept of "dynamic credentials". What this means is that rather than your application fetching credentials that have been provisioned for it in some out-of-band process, it instead requests a short-lived credential from Vault. Short-lived credentials mean the risk of a leaked password is minimal as it is only valid for a very short window of time.
Behind the scenes, Vault will create the credentials for the application on the fly. The credentials will only be valid for a configured TTL, such as 1 hour, after which the application requests a new credential from Vault.
Dynamic credentials with Hashicorp Vault are shown in the diagram below:
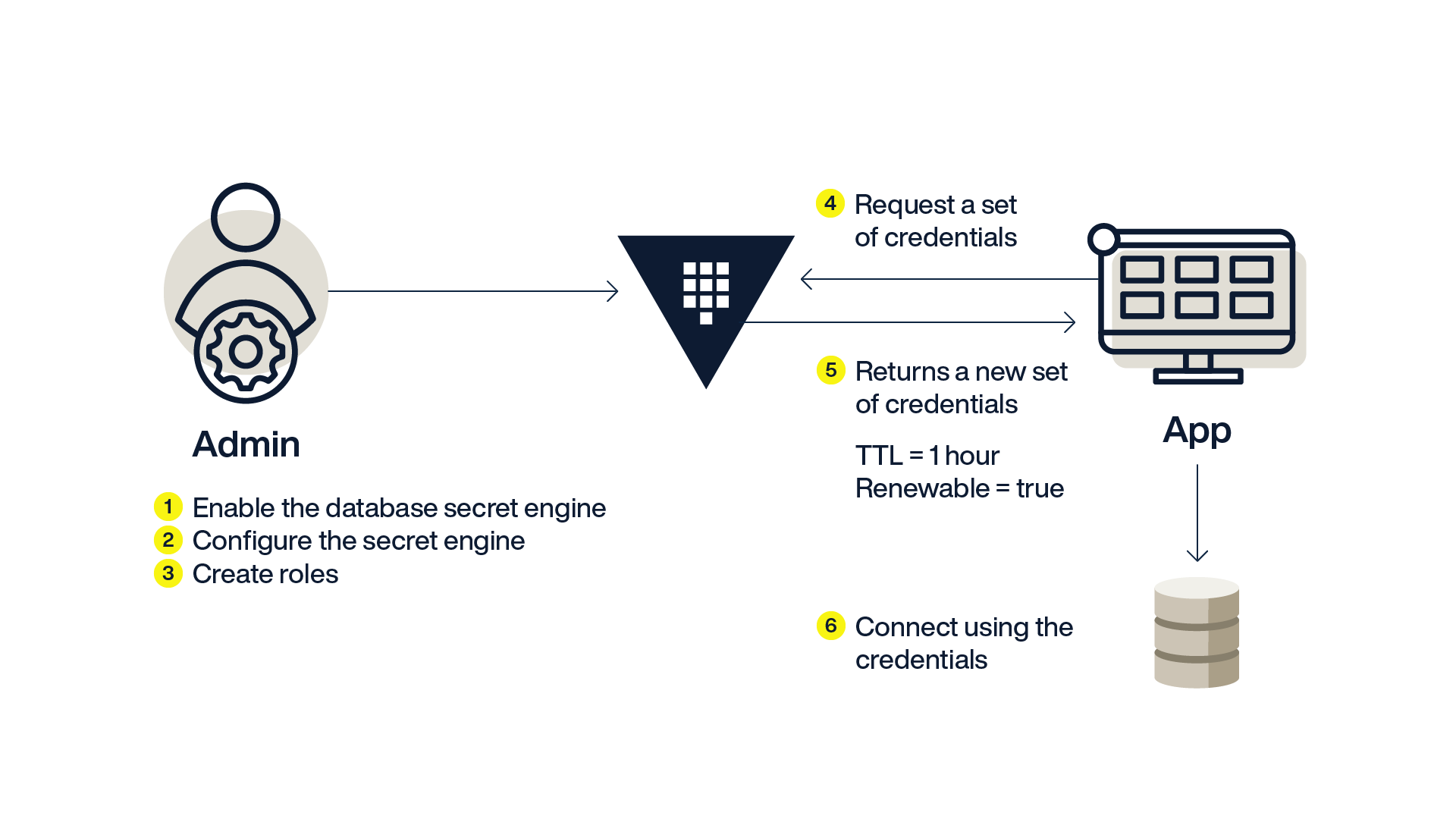
Dynamic Aerospike credentials with Hashicorp Vault
To implement this pattern in your application, you can use the community-supported Aerospike Database plugin for Hashicorp Vault.
Option 2: Use a central directory with LDAP
Another approach to protecting passwords is to manage them in a central directory with an LDAP interface such as Active Directory. In this model applications are provisioned credentials in LDAP by an out-of-band process and the Aerospike Database is configured to validate credentials using LDAP. This is often used in organizations with well established central management of users and credentials using LDAP servers.
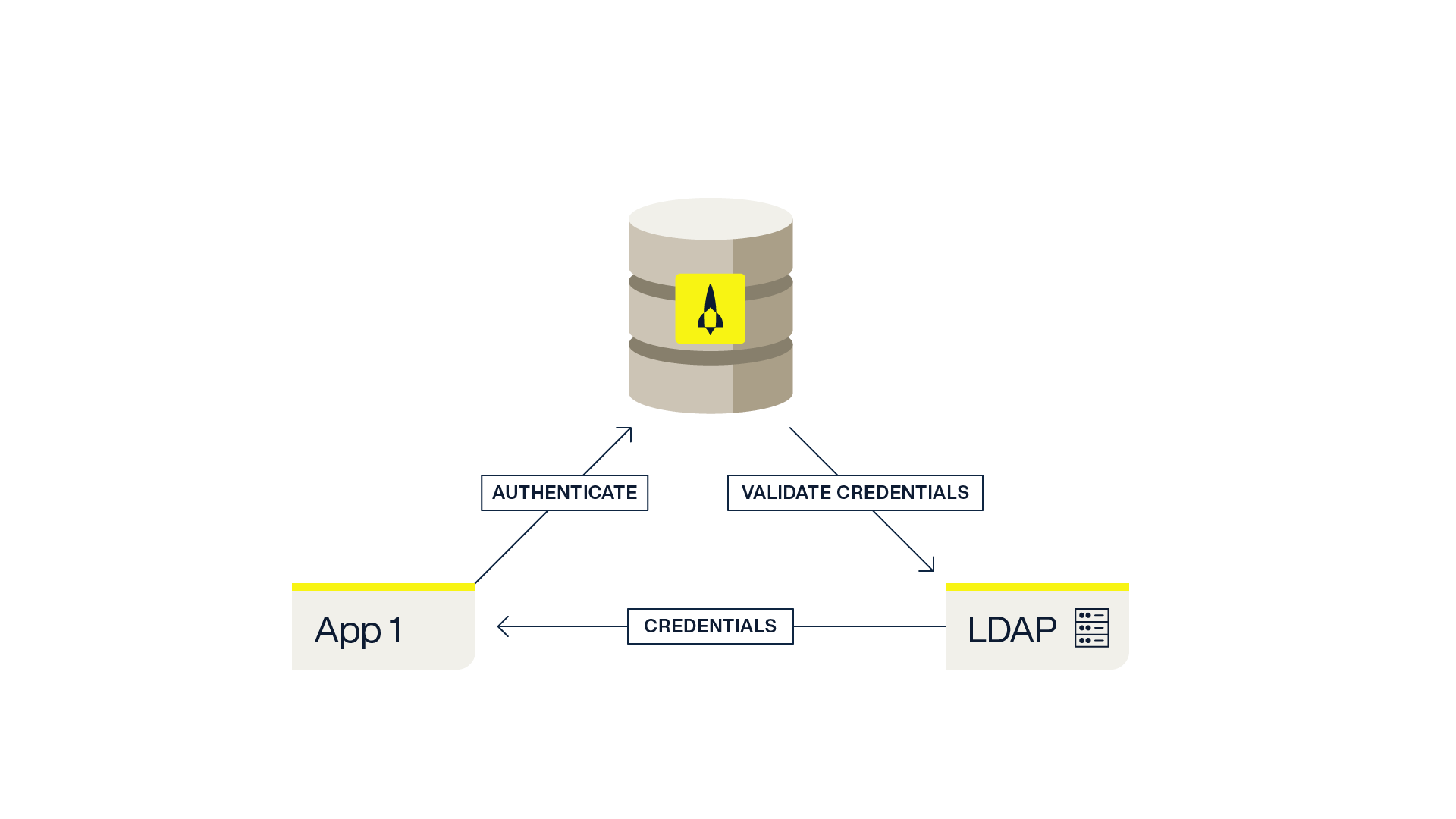
A key consideration to using this approach is that it puts the LDAP servers in the critical path of the application. LDAP systems are often not designed for the same high availability and/or scale that the application requires.
Option 3: Use PKI authentication
When using Public Key Infrastructure (PKI) authentication with the Aerospike Database the applications will not use a password at all. Instead, the application uses a TLS certificate which has the database username embedded within the certificate. The certificate itself is the “credential” that authenticates the application as a specific database user. This effectively removes the need for the application to worry about protecting the password at all. Instead, this becomes the responsibility of a TLS certificate lifecycle management solution (more on that later in this post).
Use Aerospike access control
Applications should make use of access control features of the Aerospike Database to enforce the principle of least privilege. This would mean that the permissions granted to the user the application is using are limited to only what that application needs and nothing more.
Data should be logically isolated into sets such that the data an application or user can access is scoped to just that subset of data.
For example, let’s say one application named App 1 is only reading records from SetA in the database but never writing or updating records. It would only need to have the read permission scoped to SetA. Another application named App 2 might read and modify records from SetB so it would have both the read and write permissions to SetB. And finally, a database administrator named Admin that needs to create secondary indexes and manage queries but does not need to read or write data would have the data-admin permission granted to their user.
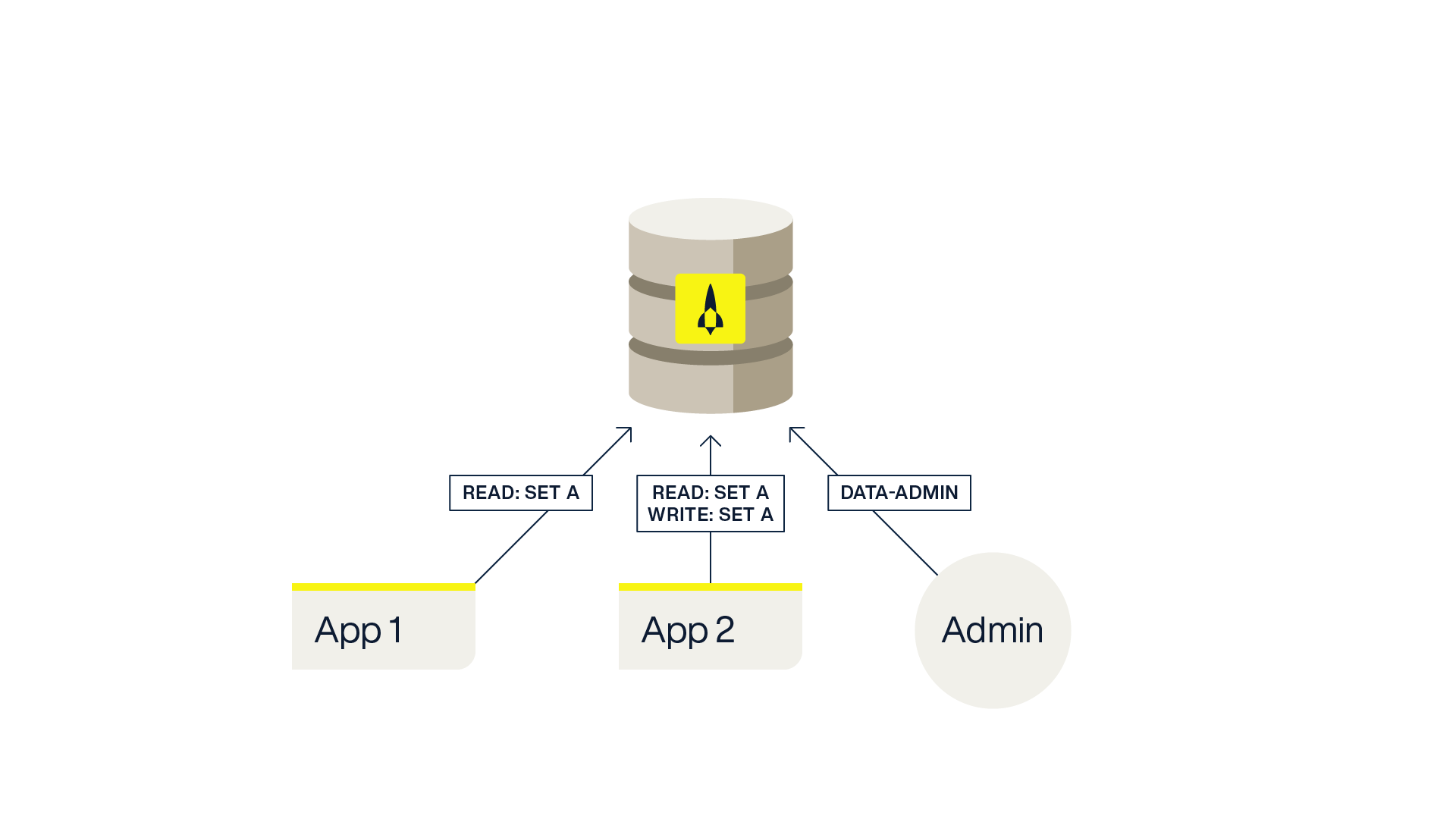
When using Aerospike Cloud, the permissions are set up for you when creating “API Keys” for your application.
Encrypt data in transit with TLS
Applications should connect to the Aerospike Database using TLS so that all data is “encrypted in transit,” meaning encrypted as it’s being transferred over a network between the application and the database.
When using Aerospike Cloud, TLS is always enabled, and TLS encryption is used end-to-end.
To see code examples that demonstrate connecting using TLS encryption in various programming languages, see the See Aerospike Client Library documentation on Connecting with TLS.
Security or compliance requirements may require applications to implement “mutual TLS” (mTLS). This is often a requirement in organizations adhering to the zero-trust security model and is a requirement if using PKI authentication. In this model both the application and database server authenticate with each other using TLS certificates.
Much like protecting passwords with a secret management solution, when using mTLS, the private keys need to be safeguarded. A TLS certificate lifecycle management solution such as Hashicorp Vault PKI secrets engine is often used for this purpose. But, more often than not, organizations already have TLS certificate management processes and tooling in place so application developers only need to know how the certificates are provided to their application.
To see fully functioning examples of using mTLS with Aerospike in Java and Python, refer to Aerospike TLS examples in GitHub.
Summary of Aerospike application security best practices
Use Aerospike authentication
Protect passwords with secret management, LDAP, or PKI
Use Aerospike access control
Use TLS encryption for data in transit
Join the Aerospike Developer community and let us know your feedback on Discord!




